고정 헤더 영역
상세 컨텐츠
본문
This version of GitHub Enterprise will be discontinued on This version of GitHub Enterprise was discontinued on 2019-03-27. No patch releases will be made, even for critical security issues. For better performance, improved security, and new features, upgrade to the latest version of GitHub Enterprise.For help with the upgrade, contact GitHub Enterprise support.
After you've checked for existing SSH keys, you can generate a new SSH key to use for authentication, then add it to the ssh-agent.
If you don't already have an SSH key, you must generate a new SSH key. If you're unsure whether you already have an SSH key, check for existing keys.
Generating a new SSH key. Open Terminal Terminal Git Bash. Paste the text below, substituting in your GitHub email address. $ ssh-keygen -t rsa -b 4096 -C 'youremail@example.com' This creates a new ssh key, using the provided email as a label. Generating public/private rsa key pair.
If you don't want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase.
Generating a new SSH key
-
Open TerminalTerminalGit Bashthe terminal.
-
Paste the text below, substituting in your GitHub Enterprise email address.
This creates a new ssh key, using the provided email as a label.
-
When you're prompted to 'Enter a file in which to save the key,' press Enter. This accepts the default file location.
-
At the prompt, type a secure passphrase. For more information, see 'Working with SSH key passphrases'.
Adding your SSH key to the ssh-agent
Before adding a new SSH key to the ssh-agent to manage your keys, you should have checked for existing SSH keys and generated a new SSH key. When adding your SSH key to the agent, use the default macOS ssh-add command, and not an application installed by macports, homebrew, or some other external source.
-
Start the ssh-agent in the background.
-
If you're using macOS Sierra 10.12.2 or later, you will need to modify your
~/.ssh/configfile to automatically load keys into the ssh-agent and store passphrases in your keychain. -
Add your SSH private key to the ssh-agent and store your passphrase in the keychain. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
Note: The
-Koption is Apple's standard version ofssh-add, which stores the passphrase in your keychain for you when you add an ssh key to the ssh-agent.If you don't have Apple's standard version installed, you may receive an error. For more information on resolving this error, see 'Error: ssh-add: illegal option -- K.'
-
Add the SSH key to your GitHub account.
If you have GitHub Desktop installed, you can use it to clone repositories and not deal with SSH keys. It also comes with the Git Bash tool, which is the preferred way of running git commands on Windows.
-
Ensure the ssh-agent is running:
- If you are using the Git Shell that's installed with GitHub Desktop, the ssh-agent should be running.
-
If you are using another terminal prompt, such as Git for Windows, you can use the 'Auto-launching the ssh-agent' instructions in 'Working with SSH key passphrases', or start it manually:
-
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
-
Add the SSH key to your GitHub account.
-
Start the ssh-agent in the background.
-
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
-
Add the SSH key to your GitHub account.
-
Start the ssh-agent in the background.
-
Add your SSH private key to the ssh-agent. If you created your key with a different name, or if you are adding an existing key that has a different name, replace id_rsa in the command with the name of your private key file.
-
Add the SSH key to your GitHub account.
Further reading
Generate Elliptic Key Pair Github 2
- 'About SSH'
- 'Working with SSH key passphrases'
| importorg.bouncycastle.util.encoders.Hex; |
| importorg.web3j.crypto.*; |
| importjava.math.BigInteger; |
| publicclassECCExample { |
| publicstaticStringcompressPubKey(BigIntegerpubKey) { |
| String pubKeyYPrefix = pubKey.testBit(0) ?'03':'02'; |
| String pubKeyHex = pubKey.toString(16); |
| String pubKeyX = pubKeyHex.substring(0, 64); |
| return pubKeyYPrefix + pubKeyX; |
| } |
| publicstaticvoidmain(String[] args) throwsException { |
| //BigInteger privKey = Keys.createEcKeyPair().getPrivateKey(); |
| BigInteger privKey =newBigInteger('97ddae0f3a25b92268175400149d65d6887b9cefaf28ea2c078e05cdc15a3c0a', 16); |
| BigInteger pubKey =Sign.publicKeyFromPrivate(privKey); |
| ECKeyPair keyPair =newECKeyPair(privKey, pubKey); |
| System.out.println('Private key: '+ privKey.toString(16)); |
| System.out.println('Public key: '+ pubKey.toString(16)); |
| System.out.println('Public key (compressed): '+ compressPubKey(pubKey)); |
| String msg ='Message for signing'; |
| byte[] msgHash =Hash.sha3(msg.getBytes()); |
| Sign.SignatureData signature =Sign.signMessage(msgHash, keyPair, false); |
| System.out.println('Msg: '+ msg); |
| System.out.println('Msg hash: '+Hex.toHexString(msgHash)); |
| System.out.printf('Signature: [v = %d, r = %s, s = %s]n', |
| signature.getV() -27, |
| Hex.toHexString(signature.getR()), |
| Hex.toHexString(signature.getS())); |
| System.out.println(); |
| BigInteger pubKeyRecovered =Sign.signedMessageToKey(msg.getBytes(), signature); |
| System.out.println('Recovered public key: '+ pubKeyRecovered.toString(16)); |
| boolean validSig = pubKey.equals(pubKeyRecovered); |
| System.out.println('Signature valid? '+ validSig); |
| } |
| } |
Generate Elliptic Key Pair Github Download
| <?xml version='1.0' encoding='UTF-8'?> |
| <projectxmlns='http://maven.apache.org/POM/4.0.0' |
| xmlns:xsi='http://www.w3.org/2001/XMLSchema-instance' |
| xsi:schemaLocation='http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd'> |
| <modelVersion>4.0.0</modelVersion> |
| <groupId>bc-examples</groupId> |
| <artifactId>bc-examples</artifactId> |
| <version>1.0-SNAPSHOT</version> |
| <dependencies> |
| <dependency> |
| <groupId>org.web3j</groupId> |
| <artifactId>crypto</artifactId> |
| <version>3.3.1</version> |
| </dependency> |
| </dependencies> |
| </project> |
commented Apr 5, 2018
|
The expected output is as follows: |
commented Sep 16, 2018
|
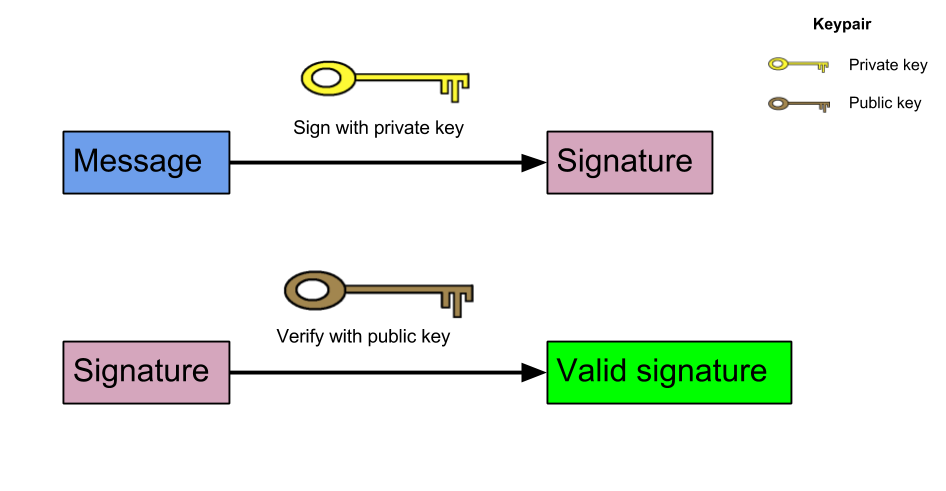
java.security package contains ECDSA classes for generating the key pair, signing and verifying signatures. These listeners remain in eye contact with you and to your presentations. Microsoft office 2016 key generator reddit. There are much more features of this utility. Microsoft Office 2016 Crack PowerPoint is mostly used in the organizations for presenting their data to its board of directors or the general public. |




